Future Trends of Cyber Security in 2018
We live in a globally connected arena where the cyber realm has been controlling all human lives. Existing in scenario like this, around all the activities are planned and depend over the internet in some ways. We are being more and more dependent over the internet. This results into the increasing significance of the internet and its ever-growing presence all over the globe. The concerned issue that has occurred in this hyper-connected era is the cyber security.

Meanwhile when internet has turned out as a place where a chunk of information is stored, cyber security comes out as a leading reason for the concern. Plenitude of data is at risk, and in turn, different lives are up for grabs. A software development company UK can create a secure and robust software that provides your business’s essential data with utmost security. Online security thus has a great to play across the world with digital professionals going to different lengths to anticipate cyber security trends in the year 2018. This post aims to highlight the crucial ones and explicate the application of those to you.
Information Combats

When data is functioning as the keyword around the world, information wars have turned out as a dominant aspect. Formerly, the main issue was data theft for economic benefits but now the criteria is quite different. Data today is more about stealing the personal data that makes our lives vulnerable. The U.S.A. presidential elections shed considerable light on the issues of cyber security of the presidential candidate Hillary Clinton. Throughout the election, people attempted to humiliate someone or an attempt to make confidential controversial data public, information wars are a growing reality that needs attention.
Security as precaution
With the evolving technology, it has become possible to predict the possible damage that may occur in the coming future even before it occurs instead of handling things after security breach has already occurred. The security set-ups need to be effective in detecting and acting instantly for managing the security issues efficiently.
Cloud storage
Almost all the companies are going gaga about the cloud storage. The year 2018 is however going to witness the security experts combating it out to safeguard cloud storage systems. With many having access and using cloud storage systems, the question will be about who can be trusted. Instability and an insecure cloud storage system are likely to arise. A cloud decision model controlling the personal and public use of cloud storage will probably be designed by companies to protect all the information stored in cloud storage.
Nation state wars
Online security, these days, has undergone a multitude of cases where the issues occur between two nations. Online security conflict or data theft between two different nations is treacherous and will be having intense backlashes on the global political scenario. They will be on a rise and the extent of the issues will only nurture.
Challenges Posed By IOT
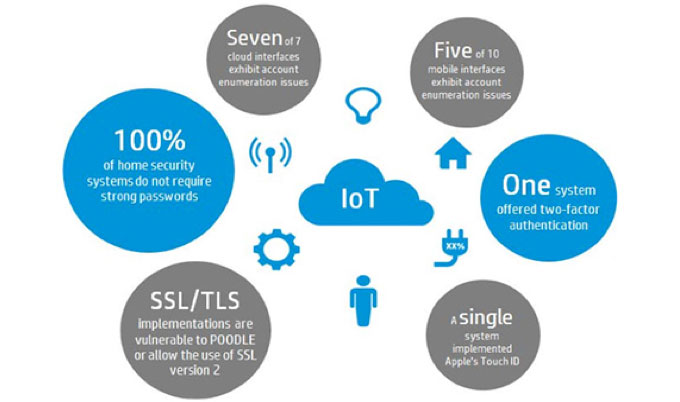
This influential phenomenon has been adopted by different enterprises and the devices integrating this new age technology are not secure enough. Many personal data becomes vulnerable throughout. Default passwords and defective communication methods are the heart of faulty security apparatus. Violation of privacy because of IOT’s growing applications will keep on rising in 2018.
IOT connected smart cars have been already launched in the market. Driver-free automobiles and other vehicles will be ruling the future. Already numerous big companies are investing their money into the new IOT connected smart cars. The time is not far when we might be using them on the roads. A study by BI predicts that there will be nearly 94 million connected cars by the year 2021.
The near future is Internet of Things Wearable devices. Users are able to regulate your car through their wearable devices like smartwatch to do tasks such as automatically parking it and opening and closing the gates. Your wearable device may also sense the dangers around you. People are already using the devices that are tracking our activity and workout routine. In the coming future, we can also track our calorie consumption and eating habits automatically. Therefore, everything will be easy excluding that making every single thing easy is difficult.
The governmental action and legal clauses
The surveillance laws of the government are changing and this is likely to have an effect on the cyber security of different companies. The finances involved in business are likely to be altered when new laws come into force regarding data management and protection. Harmonization changes and implementation of these laws might take a little time but the effects will definitely be seen in 2018.
Digital ecosystems
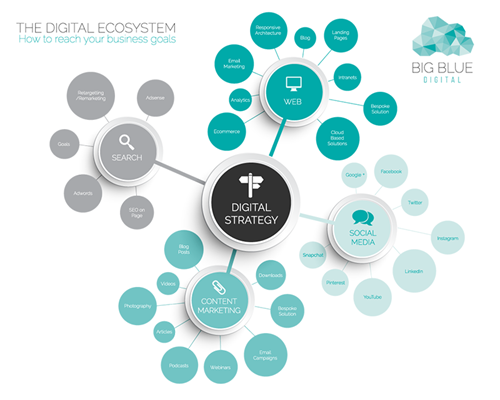
Each individual assumes a vital part in an advanced biological community. With security, security and different factors in question, each individual has a part to play in the assurance of information. Security and the unwavering quality factor assume real parts in such manner. An idea about security subsequently turns into an unquestionable requirement for computerized biological systems.
Information science and information examination are the following enormous thing. These basically manage the checking of a lot of information and downplaying human practices and foreseeing patterns in view of these expansive arrangements of information. Any break that happens leaves this whole measure of information helpless. Digital security is therefore a worry that maladies everybody. It isn’t just confined to huge firms and organizations yet concern each p erson as their own information may be in question.
Computerized reasoning is required now to handle the issues. More current innovation managing digital security with a quick strategy for forecast of ruptures in light of provisos and blemishes is fundamental for the best possible security of information and the internet. Preparing of security specialists to manage across the board security concerns should be the foundation of things. Programming outsourcing is another angle that demand keen consideration while being managed. Digital security patterns are many however to guarantee the security of lives and individual data, this is a region that requests consideration, investigation and care.

